Like how we are restricting access using firewall, in kubernetes cluster you can restrict access of pod using network policy. Network policy is used to restrict the access of pod to pod communication in cluster. As a prerequisite you have to install any available network plugin such as calico, flannel, etc. Network plugin implements network policies. To use network policies you must use networking solutions.
Here the pod can communicate with other pod using IP addresses. Each pod is assigned with IP address.
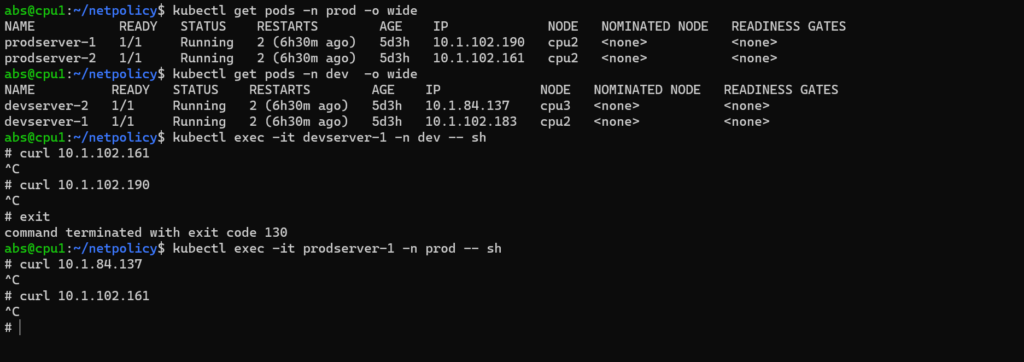
To explain about network policy here we are taking two namespaces such as dev, prod. Each namespace consists of two pods.

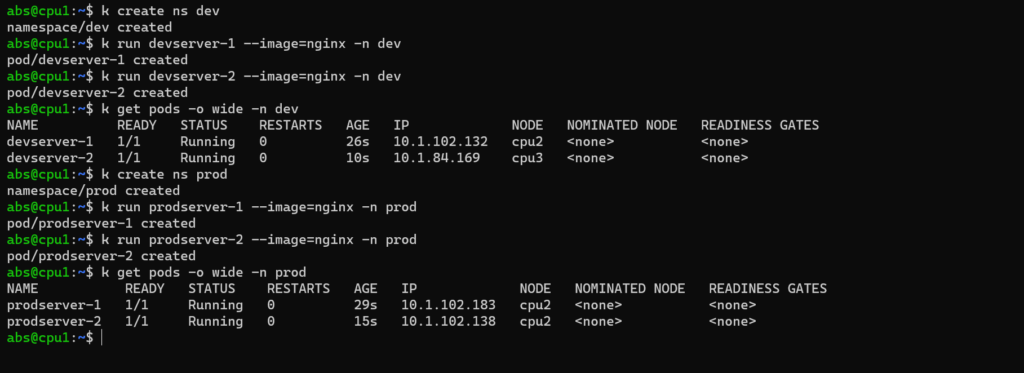
Now we will see how the pod is getting communicated within namespace and form other namespace.

Here the pod can communicate with each other in same namespace. Now we will see whether the pod can communicate from other namespace as well.

Clearly, we can see that pod from prod namespace can communicate with pod from dev namespace.
The Network Policy Resources
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector: # The network policy applies to the pod with label role=db.An empty pod
matchLabels: #selector selects all the pods in the namespace.
role: db
policyTypes: #Policy type could be ingress or egress
- Ingress
- Egress
ingress: # Ingress policy type specifies that incoming traffic to the pod.
- from:
- ipBlock: # It allows incoming traffic from pod with the following IP
cidr: 172.17.0.0/16
except:
- 172.17.1.0/24
- namespaceSelector: # allows incoming traffic from pod with the following namespace
matchLabels:
project: myproject
- podSelector: # allows traffic from this particular pod.
matchLabels:
role: frontend
ports: # allows a particular protocol and port.
- protocol: TCP
port: 6379
egress: # Egress specifies outgoing traffic.
- to: # allows outgoing traffic from the pod where we apply network policy to this pod with the
- ipBlock: #follwoing IP address
cidr: 10.0.0.0/24
ports: # allows a particular protocol and port.
- protocol: TCP
port: 5978
1.Namespace selector and Pod selector
If we want to allow a traffic to/from a particular pod from particular namespace then we can define network policy as follows.
ingress:
- from:
- namespaceSelector: #
matchLabels: #
tier: database # Allows after matching
podSelector: # namespaceSelector AND podSelector
matchLabels: #
role: db #
2.Namespace selector or Pod Selector
If we want to allow a traffic from a particular namespace or from a particular pod then we can apply the network policy rules as follows
ingress:
- from:
- namespaceSelector: #
matchLabels: #
tier: database # Allows after matching
- podSelector: # namespaceSelector OR podSelector
matchLabels: #
role: db #
1.Default deny all Ingress Traffic
It denies all the incoming traffic to that particular pod from the defined namespace. Let’s see how it denies all the incoming traffic to that particular pod.

Here we are trying to connect prodserver-2 in prod namespace from prodserver-1. The pod is getting connected. Now we will apply the default deny all ingress network policy and test the applied rules. Apply the network policy rules as follows
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny-ingress
namespace: prod
spec:
podSelector: {}
policyTypes:
- Ingress
Here we are applying default deny all ingress traffic in the prod namespace. An incoming traffic to the pod in the prod namespace will get restricted. Let’s see it.

Here we are trying to connect a pod podserver-2 from prodserver-1.From this picture we can clearly seen that prodserver-2 is not getting connected at all.
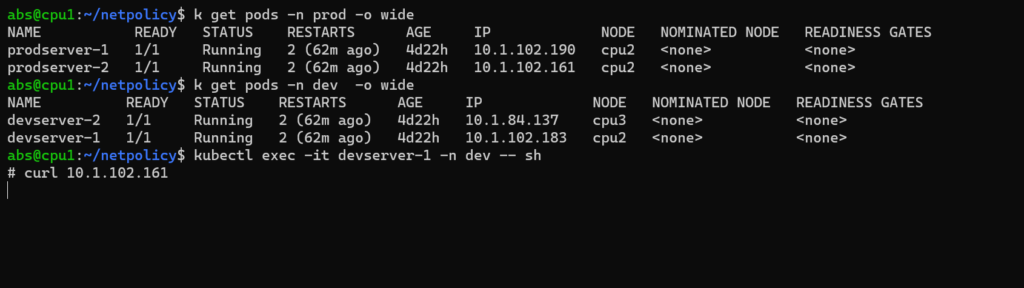
Here we are trying to connect prodserver-2 from devserver-1. prodserver-2 is not receiving any incoming traffic. So the applied network policy is clearly working.
2.Default Deny all egress traffic
If you want to restrict an outgoing traffic from all the pod in a defined namespace you can apply default deny all egress traffic.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny-egress
namespace: prod
spec:
podSelector: {}
policyTypes:
- Egress
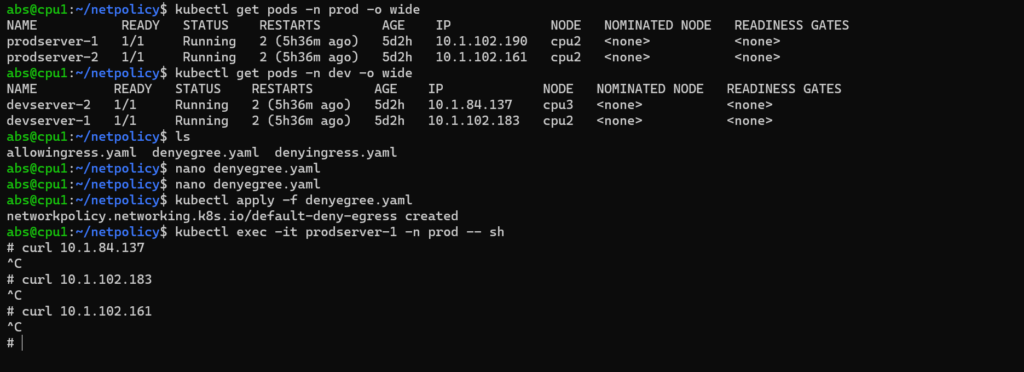
Here default deny all egress traffic in prod namespace. So we are testing it from that namespace.
Logging into prodserver-1 and try to send traffic to all other pods within namespace and also pods in different namespace. From this picture we could understand that prodserver-1 couldn’t send traffic to any other pods.
3.Allow all ingress traffic
If you want to allow all incoming connections to all pods in a namespace, you can apply allow all ingress traffic network policy.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-ingress
namespace: prod
spec:
podSelector: {}
ingress:
- {}
policyTypes:
- Ingress

Logging into devserver-1 and try to send an traffic to prodserver-1. It is allowing traffic.
4.Allow all egress traffic
If you want to allow all outgoing connections from pods in that namespace then you can apply allow all egress traffic network policy.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-egress
namespace: prod
spec:
podSelector: {}
egress:
- {}
policyTypes:
- Egress
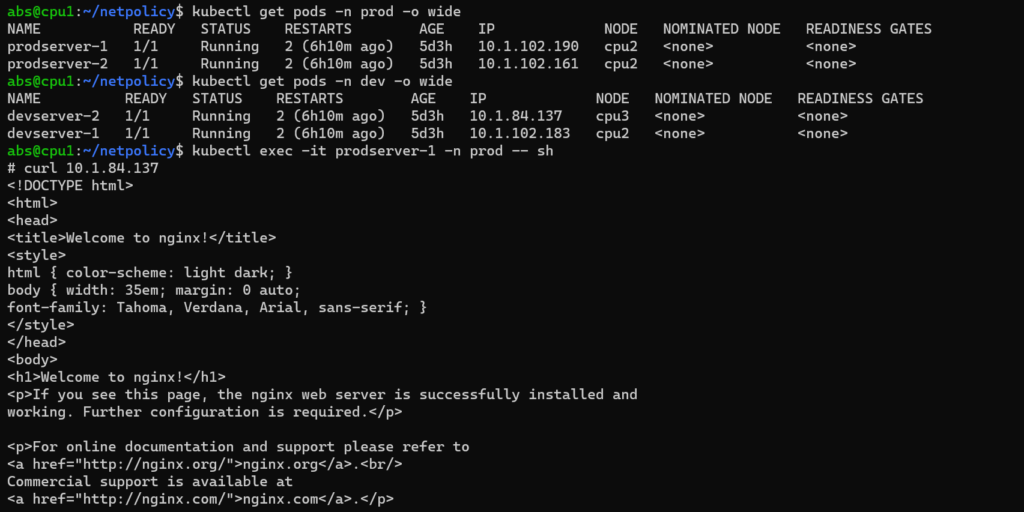
Here from prodserver-1 we are sending an outgoing traffic to devserver-2 .The outgoing connection is allowed.
5.Default deny all ingress and all egress traffic
If you want to apply a policy that won’t allow any incoming traffic and outgoing traffic in a defined namespace then you can apply this policy as follows.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny-all
namespace: prod
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
From this picture we can clearly seen that incoming traffic and outgoing traffic from all pods in that prod namespace is restricted.
