Decode/Decrypt the Kubernetes Secrets
In this blog post, we will explore the process of decoding and decrypting Kubernetes secrets, and how you can safely reveal their information without compromising security.
Decoding or decrypting Kubernetes secrets is a crucial task for Kubernetes administrators and developers who need to access sensitive information such as API tokens, passwords, or other confidential data stored within a Kubernetes cluster. Kubernetes secrets are encoded in base64 and can be encrypted at rest, depending on the configuration of the cluster. Below, I’ll provide a step-by-step guide on how to decode and decrypt Kubernetes secrets.
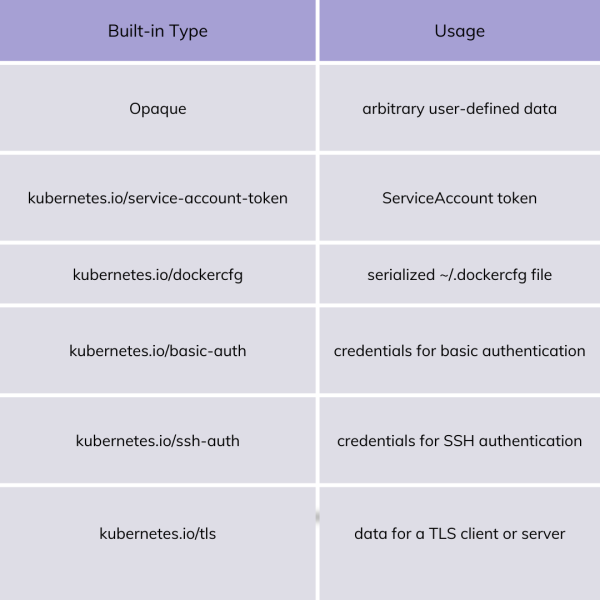
Types of Secret
Steps to Decode the Kubernetes Secrets
1. Create a Kubernetes Secret
kubectl create secret generic my-secret --from-literal=username=admin --from-literal=password=secret
secret/my-secret created
2. List Secrets
To identify the secret you want to decode, you can list the secrets in a specific namespace using the following command.
kubectl get secrets -n namespace
# Replace with the namespace where your secret is located.
3. Retrieve the Encoded Secret
Once you have identified the secret you want to decode and decrypt, retrieve it using the kubectl get command, specifying the secret’s name and output format in JSON.
kubectl get secret -o json
4. Decode the Secret
You can use the base64 command to decode the secret. Replace <base64-encoded-data> with the actual encoded data you obtained from the kubectl get secret command.
echo -n "base64-encoded-data" | base64 --decode
# To decode a specific value from a secret directly
kubectl get secret secret-name -n namespace -o jsonpath="{.data.password}}" | base64 --decode
After decoding, you can use the secret in your application or for any necessary tasks. Decoding and decrypting Kubernetes secrets are essential skills for maintaining and troubleshooting your Kubernetes applications effectively. Remember to handle the decoded secrets with care and ensure that sensitive information is protected. It’s essential to have proper RBAC (Role-Based Access Control) and encryption in place to secure secrets within your Kubernetes cluster.
